How Twitter Account Owners’ Passwords Get Hacked Without Them Knowing [Tutorial 2022]
Twitter is one of the most trending sites. In this guide, we will be discussing how to hack Twitter account password easily without letting your victim know!
Twitter Inc. is a social media platform where one can easily share news, messages and media (images, audio, video).
Where there is a trend, there is also is a security threat of losing account access or worse someone gaining access to yours.
Why would someone do that?
Well there are lot of details on profiles that is hidden and they can be useful if accessed.
Also, once a hacker gets access to your account, they can read your personal messages and also tweet on your behalf.
Hack Twitter account password – Ultimate Guide 2019
The financial benefit of hacking accounts:
Well, hackers have not only posted absurd content, they have been successfully stolen a lot of unique twitter handles, of some twitter users who run their accounts for business. These hacked accounts were released by asking for ransom for their account. Their data and followers being on stake, this locked account have troubled a lot of users.
Now you might be wondering how can someone do that?
Hacking is a professional task but to hack a twitter account, it’s not a big deal.
It’s not like you are safe guarded against getting hacked. Well, if you are still curious about how can someone hack into a Twitter account, this article will tell you some.
You need not be a programmer to hack into someone’s account, you just need to make use of resources and some ideas. It’s never too easy, but never impossible.
1. Hack Twitter – The password guessing game
If you know someone who’s account you want to access, this method is apt.
Since you know the person, you could try guessing the password, or if you know they don’t keep a strong password or the same one for all the accounts, you can directly access the account using the password you think you know.
It’s just an option if you are lucky enough to know what someone’s password might be.
Another method is looking over the shoulder of someone silently when they are logging in.
This will give you if not an exact, but some idea what the password might be, say you saw someone enter a few characters that make up their favorite book and followed by digits; you could easily try a few combinations and gain access.
If the target has the habit of writing down their password, in an app or a notebook, it is easier knowing their password and logging in.
Well that is known as “Shoulder Surfing“!
But of course you know these, read on for some more interesting hacks.
2. Hacking twitter password with SS7
This method is a little technical.
The SS7 is a protocol that was used in 1970 where one network could talk to another.
You need a computer with Linux and an SDK for SS7.
Once you have access to a SS7 system, you can intercept all the data sent and received on a device.
So, after setting up your SS7, you need to enter the phone number of the twitter account user, your target.
Then you can go to password reset option using phone number. This will send a verification code to the user’s mobile number.
You can read this text on your SS7 system, enter the code and change the password yourself.
Once changed, you can login using the set password and the twitter account of the target is now compromised.
3. How to hack Twitter account using Phishing
Thousands of accounts have been compromised because of this popular attack.
It literally steals your account credentials in quite an easy way.
Let’s see how does this work:
1. Sending a Spam message to the user in form of a DM or a tweet. This message should contain a phishing link in order to view something – a picture or video or some blog web link.
2. When the target clicks on the link, they are redirected to a fake login page. This page will look like the twitter login page, but it is not. It is your phishing page.
3. You can make this page to redirect the user to the session. You are not truly authenticating the user, so even if the user enters incorrect credentials, the user will be redirected to session.
4. But what is entered by the user is what we are looking for. You can fetch the data entered by the user at the fake twitter login page and then you have stolen the user’s credentials.
5. These credentials can be used in to log in to the user’s Twitter account.
This method is very easy, even a guy with average knowledge can execute this! Wanna know how to?
Read our MOST RECOMMENDED phishing guides below:
- Best working phishing trick 2018 – Shadowave
- Hacking Facebook, Twitter or any other site using Phishing
- Hack Wifi using Phishing Method !
- Umbrella Dropper- Ultimate Phishing tool
4. Social Engineering – Hacking Twitter online free
Social engineering is a technique of manipulating users into revealing confidential information.
This information can be used to gain unauthorized access their online accounts, here say, Twitter.
The term “Social Engineering” also involves actions that makes use of exploiting human traits kindness, greed, and curiosity to gain access to their personal accounts or getting the users to installing backdoor software through which one can gain such access.
Hackers have a lot of tricks up their sleeve that make target users release vital login information. It is a very carefully planned process.
Gathering of Information:
This is the first step, wherein the hacker needs to learn as much as he can about the intended victim.
The information could be gained from a lot of places, mainly from the target’s own user profile, or other social networking sites and sometimes by talking to the users of the target system.
What kind of information are we looking for?
Mostly things the target is keen about.
Through likes and following accounts, one can know what the target user likes and dislikes, what kind of trends the user follows etc.
Planning the Attack:
A hacker needs to create an outline how he or she intends to carry out the attack.
Acquiring Tools:
Some computing help is needed to perform attacks. The hacker gathers tools that will be used to launch the attack
Attack:
Using all the resources we now need to carry out the attack.
Using the acquired knowledge:
Information gathered during the social engineering process such as pet names, birthdates of the organization founders, etc. is used in attacks such as password guessing.
Say one is a fan of DC Comics and adores The Joker. He constantly posts clippings from comics and movies.
The user has set his password as with his birth date say something like WhySoSerious1206.
This is easy to guess and try.
The phishing attack can also be carried out using social engineering.
The hacker can create a link to user’s interests, say in this case, Top 10 Joker moments of all time.
The user is bound to click on such links and will surely sign in if asked.
5. Hack Twitter Password – Keylogging Malware
If you could lure the target to log in to an un-safe system, this keylogging attack is easy.
For more info read: All About Keyloggers : Description, Methodology & Working
You just need to install a keylogging application on your system and make them login.
If not that, one can inject a keylogging malware into the user’s own system.
Through web links and email attachments, one can achieve this.
The only catch here is the malware shouldn’t be detected by an antivirus software that user might have installed.
There have been cases where to view a certain video, users were asked to install the latest version of Adobe Flash Player that was a disguised malware.
What does this help hackers do? You get a log of all the keys used by the user and it is easy to extract the user id and password combination out of it. And the hacker can smoothly access the credentials.
You may like to read: How To Hack Users Credentials Using Remote E-mail Keylogger!
6. Using password finding tools
Usually, session data is stored on any device and browser in encrypted form.
In order to use it to login one must be able to decrypt it.
There are tools and software that allow you to retrieve login details saved by most browsers like Chrome, Opera, Internet Explorer, etc.
If you are looking to hack into someone’s account, you will need to let them use your computer or gain access to theirs, this is because these tools only reveal the password a user has used to login to the device using session data stored by browsers.

SterJo Twitter Password finder is one such windows tool that is developed to retrieve password of a twitter account.
It is lightweight with an easy to use interface that doesn’t require much technical knowledge.
By a simple click of a button, one can retrieve the password and copy it to clipboard.
Just paste it in a text document to reveal it.
There are a lot of websites and apk tools that help you with hacking twitter accounts using the above methods.
These tools only ask you to enter user credentials like email and/or username and they help you gain password.
You could also install a spyware on target’s phone that gets you keylogging details or helps you read SMS for password reset code. Spyware apps like mSpy and FoneMonitor.
7. How to hack a Twitter account easily?
A hacker group finally found a flaw allowing anyone to hack a Twitter password in less than 2 minutes from a username or phone number or email address.
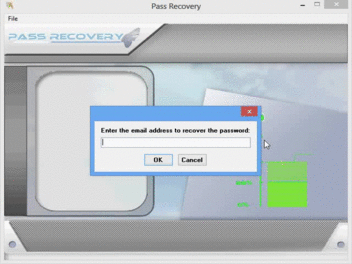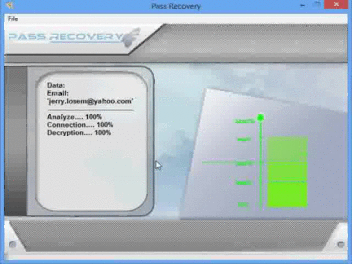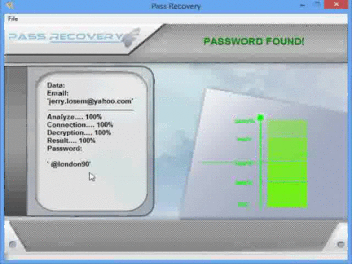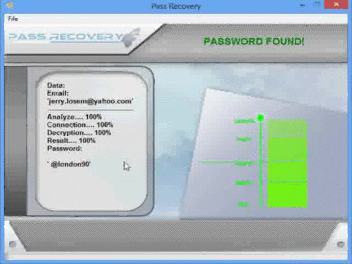
Now, everyone can hack a Twitter account without being a computer scientist!
The software’s name is PASS RECOVERY and it can be downloaded from the link https://www.passwordrevelator.net/en/passrecovery.php
Safeguarding your own Twitter account
There are endless ways in which a Twitter account can be compromised.
We need to try and keep the hackers at bay.
There are a lot of ways in which these hacks can be avoided:
· Keep strong passwords. Easy passwords that anyone could guess are easier to hack. Passwords like abcd123456 are more commonly used than complicated ones. Try following password strength guidelines.
· Use different passwords for different accounts. If in case your Twitter account is compromised, the hacker will sure try to use the same for your e-mail or even bank log in and it could lead to huge loss.
· Do not click on unknown links. Check the url (located at the top of the browser) before logging in to any website. The phishing urls are not exact, there is a bot (similar looking url) used most of the times.
Do not download third party applications on your phone or desktop. These might be malware or spyware.
· Disable access to unknown and unwanted applications from twitter. Your account might be hacked through these.
· Do not share your password over phone calls and emails. Beware of phishing texts that ask you to change your password. Always use official twitter link to reset password.
Also read: How To Secure Your Password From Hackers : Tutorial
Online security is our responsibility. Don’t illegally hack into someone’s account.
![Untitled Design (8) How To Hack Twitter Account Password Without Them Knowing [Tutorial 2018]](https://hackeroyale.com/wp-content/uploads/2018/07/Untitled-Design-8.jpg)
Comments
Post a Comment